News of a big brand suffering a data breach is all too common today. But if you don’t get an email from such a company, you could mistakenly be thinking it doesn’t affect you. The thing is, large breaches are happening all the time. Cybercriminals then put access...
IT Security
How to Protect Your Proprietary Information
Proprietary information makes your business special, whether you’re a tech startup with a smart algorithm or a food manufacturer with a secret sauce. Regardless of industry, business gains competitive advantage from distinct practices or unique data. The last thing...
Healthcare Providers Must Prepare for IT Disasters
Healthcare professionals regularly handle the worst. Whether its broken bones, horrible abscesses, disease, or death, but that doesn’t mean they’re ready for all that can cripple their technology. In 2011, one of the deadliest tornadoes in U.S. history destroyed a...
How To Stay Safe While Being Social
How to Stay Safe While Being Social People happily share their private information online, building robust libraries that can easily become a one-stop goldmine for fraudsters. It’s not exactly the intention everyone has when they sign up, as the whole point of...
3 Cyberattackers Putting Business at Risk
Cyberattacks and data breaches happen worldwide, and no one is immune. Your business needs to protect its networks and systems, and secure sensitive data. But how much do you know about the types of cybercriminal out there. This roundup discusses the biggest threats...
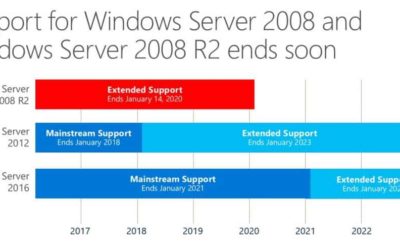
Don’t let the end of Windows Server 2008 Sneak up on you
Don’t let the end of support for Windows Server and SQL Server 2008 sneak up on you—the impacts to security and costs are too important. Avoid business disruptions and use this as an opportunity to adopt the most current security and innovation technologies. Support...
Lawyers: Stop Making These Common Tech Mistakes
Cyber attacks in the legal industry are on the rise. Law firms of all sizes face threats such as business email compromise, denial-of-service, phishing, data exfiltration and ransomware. Yet, your lawyers could be...
The Real Advantages of a Virtual LAN (VLAN)
There are many acronyms to keep track of in the IT realm. One that’s been around for over 30 years now is VLAN – virtual local area network. A VLAN offers flexibility that more and more businesses find appealing. But what exactly is a VLAN? A VLAN allows you to...
The True & Unexpected Costs of Being Hacked
There are the normal costs everyone associates with a breach, like getting your own server and computers fixed up, with maybe a little downtime. But really, most businesses view the possibility of getting hacked as more of an inconvenience than a bottom-line cost. For...
Ring in the New Year with New IT
For many of us, 2021 can’t come soon enough, and we're hoping next year will be a better one. One way to get the best start in the new year? Take the time now to review business technology. There are several areas that you might improve to support 2021 success. First,...
Is Misconfiguration Making Your SMB Vulnerable?
Cybersecurity attacks on big-name brands or governments are familiar headlines these days. Millions of access credentials are breached, and millions of dollars are lost to ransomware attack. You may think you’re protected, but a single undetected misconfiguration...
Disk Encryption Protects Your Personal Computers
Always wanted to feel like a secret agent? Well, here’s your chance! Did you know you can encrypt your hard drive to protect the data on your computer? This is a good way to secure your information, whether at home or on the move with a laptop. Setting up encryption...
Why You Need Both Software and Hardware Firewalls
A firewall sounds like a pretty intense thing – unless you’re an action-movie stuntman. Yet when it comes to internet security, you may not have as much firewall protection as you need. Many internet security products bundle antivirus and firewall software, and many...
Wi-Fi Trends
The demand for faster and more reliable wireless network connections has never been greater. With the advent of smart phones, tablets, printers and IoT devices more and more devices are entering the network space. When choosing the right solution for your network...
Don’t Fall Victim to COVID-19 Cyber Security Threats
I.T. already has enough to worry about with COVID-19 sending everyone home to work. Too bad cybercriminals are such opportunistic creeps: they’re even taking advantage of the global health pandemic to scam the unsuspecting. This ebook highlights many...
5 Red Flags of Phishing Emails: Think Before You Click
A single click can be the difference between maintaining data security and suffering massive financial losses. From the moment just one employee takes the bait in a phishing email, your business is vulnerable to data breaches and extensive downtime. Quickly spot the...
Protect Your Firm Against Zero-Day Attacks
Protecting your business against the latest IT threats should always be a top priority. Updating antivirus and patching your operating system is a great way to start. What happens, however, when a threat appears at your door before security firms have had a chance to...
Steer Clear of Coronavirus Scams
With the world grappling with a health pandemic, scams are shocking. Regrettably, bad actors are everywhere, always looking for opportunities, and they’re seeing one in the coronavirus. This article outlines what you need to watch out for and how to stay cyber safe....