NEWS
Recent News
Building a Smart Data Retention Policy: What Your Small Business Needs to Keep (and Delete)
Does it ever seem like your small business is overwhelmed with data? This is a very common phenomenon. The digital world has transformed how small businesses operate. We now have an overwhelming volume of information to manage employee records, contracts, logs,...
Avoid Cloud Bill Shock: Cost Optimization Tips Every Small Business Should Know
The cloud can be your greatest asset or your biggest financial headache. One minute you’re deploying apps and scaling infrastructure, and the next you’re hit with a cloud bill that strains your budget.Sound familiar? It's a common business problem. A study by Nextwork...
Simple Backup and Recovery Plans Every Small Business Needs
What would happen if your business lost all its data tomorrow? Would you be able to recover, or would it grind your operations to a halt? Every small business runs on data, which includes customer information, financial records, communications, product files, and...
Previous News
Healthcare Providers Must Prepare for IT Disasters
Healthcare professionals regularly handle the worst. Whether its broken bones, horrible abscesses, disease, or death, but that doesn’t mean they’re ready for all that can cripple their technology....
How To Stay Safe While Being Social
How to Stay Safe While Being Social People happily share their private information online, building robust libraries that can easily become a one-stop goldmine for fraudsters. It’s not exactly the...
3 Cyberattackers Putting Business at Risk
Cyberattacks and data breaches happen worldwide, and no one is immune. Your business needs to protect its networks and systems, and secure sensitive data. But how much do you know about the types of...
5 Benefits of Windows Virtual Desktop for Businesses
The days of doing all our work in the office are gone for most businesses. There are clients to meet, conferences to attend, and roadshows to run. Employees are often on the move, and they want to...
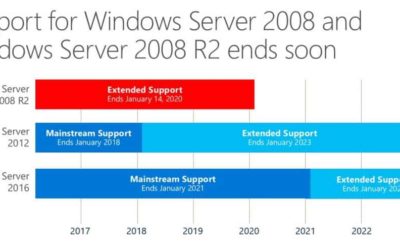
Don’t let the end of Windows Server 2008 Sneak up on you
Don’t let the end of support for Windows Server and SQL Server 2008 sneak up on you—the impacts to security and costs are too important. Avoid business disruptions and use this as an opportunity to...
Why MSP Support Beats a Break-Fix Approach
Computers break at challenging times. Always. And there’s no worse time than the holiday season. Your employees want to spend time with family and friends, relaxing and reminiscing. They do not want...
The Real Advantages of a Virtual LAN (VLAN)
There are many acronyms to keep track of in the IT realm. One that’s been around for over 30 years now is VLAN – virtual local area network. A VLAN offers flexibility that more and more businesses...
E-accounting: Top 3 Considerations for Online Client Meetings
Many businesses were teleconferencing before COVID-19. After all, meeting virtually saves both you and your client time, and busy business owners often don’t want to spend the time to make a trip to...
7 Benefits of Cloud Computing for Accountants
The public cloud services market has grown dramatically, and, according to Gartner, migrating to the cloud is a top priority for a third of companies. Analysts predicted the market would reach $266...
Dial up Telehealth Security
The use of telehealth has been growing rapidly over the past decade. Then, the coronavirus pandemic prompted another jump in telehealth offerings. There are many advantages to digital healthcare,...
The True & Unexpected Costs of Being Hacked
There are the normal costs everyone associates with a breach, like getting your own server and computers fixed up, with maybe a little downtime. But really, most businesses view the possibility of...
Ring in the New Year with New IT
For many of us, 2021 can’t come soon enough, and we're hoping next year will be a better one. One way to get the best start in the new year? Take the time now to review business technology. There...